An overview of MITRE's Malware Behavior Catalog (MBC) framework and MBCScan, a command-line tool I built to surface MBC behaviors from Capa scan results.
Read more →Talking about Mitre's Malware Behavior Catalog
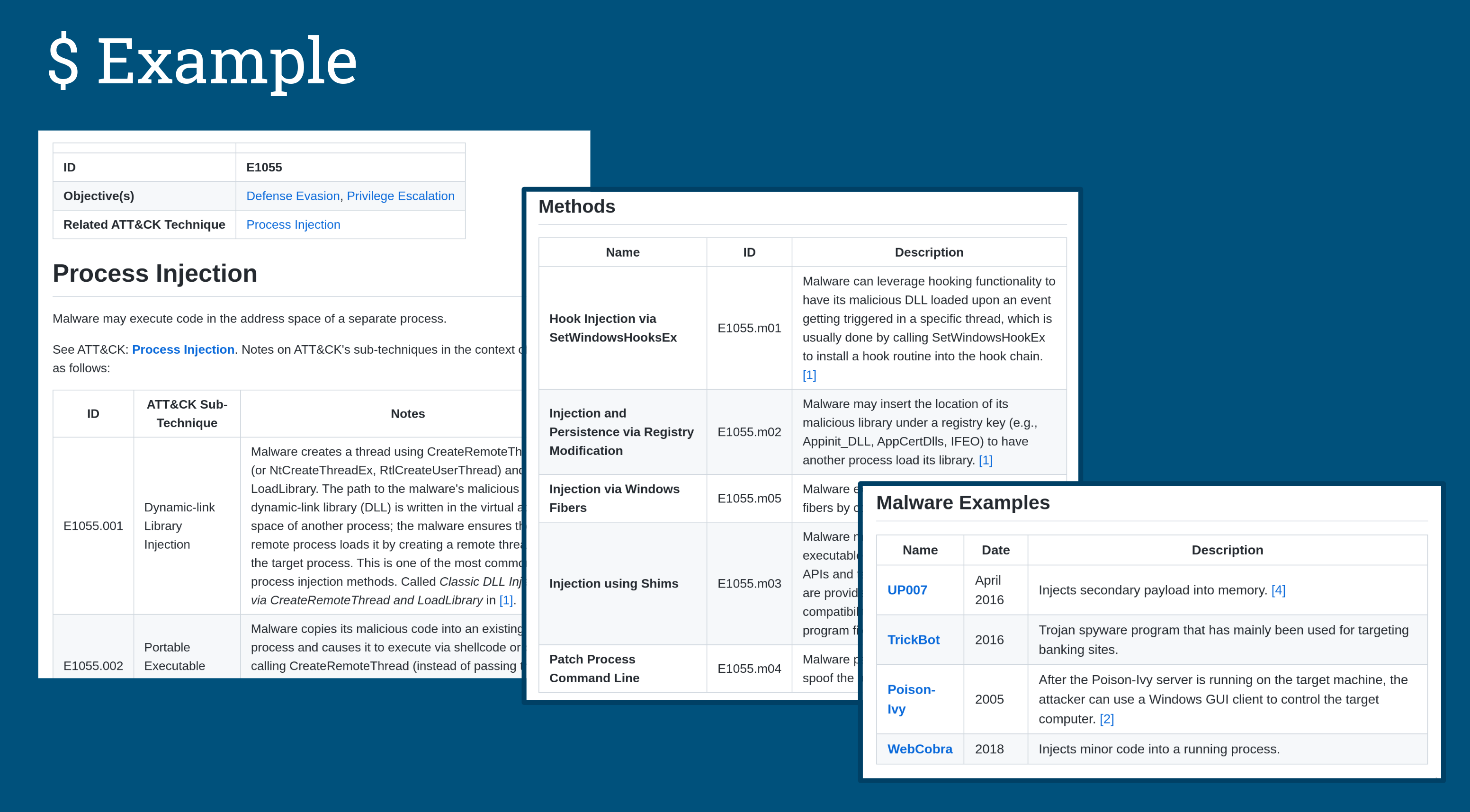

An overview of MITRE's Malware Behavior Catalog (MBC) framework and MBCScan, a command-line tool I built to surface MBC behaviors from Capa scan results.
Read more →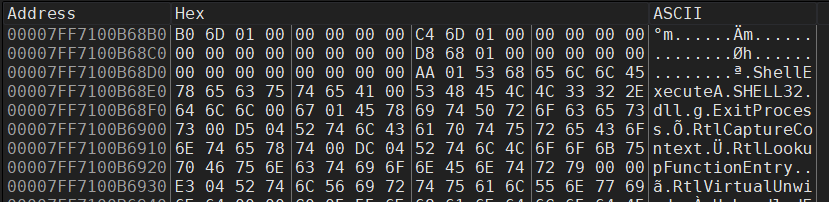
How to hide API call strings from antivirus detection using LoadLibrary and GetProcAddress for runtime DLL loading, with a full x64 assembly implementation.
Read more →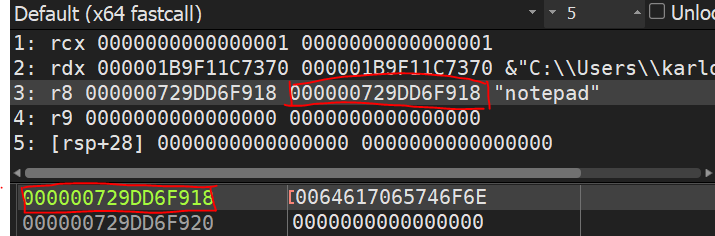
How to hide strings from antivirus detection by placing them on the stack instead of the .data segment, demonstrated in C and x64 Windows assembly.
Read more →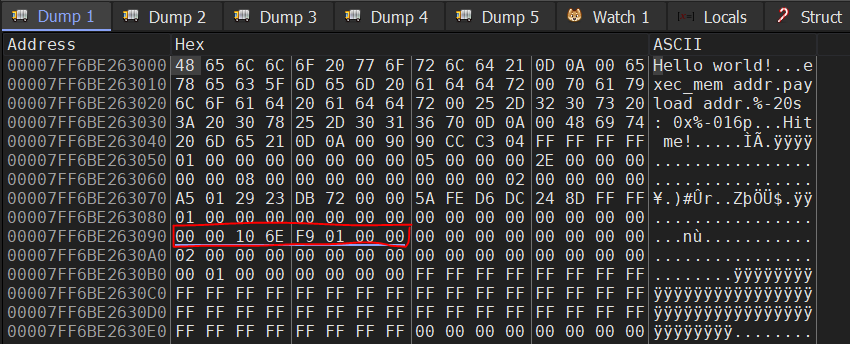
Practical lessons from converting a C malware dropper to x64 Windows assembly, covering shadow spaces, calling conventions, and memory segments.
Read more →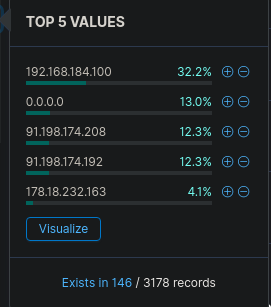
CyberCorp Case 2 part 3 — certutil download, LSASS dumping, WMI lateral movement to a domain controller, and tracking the second reverse shell C2 address.
Read more →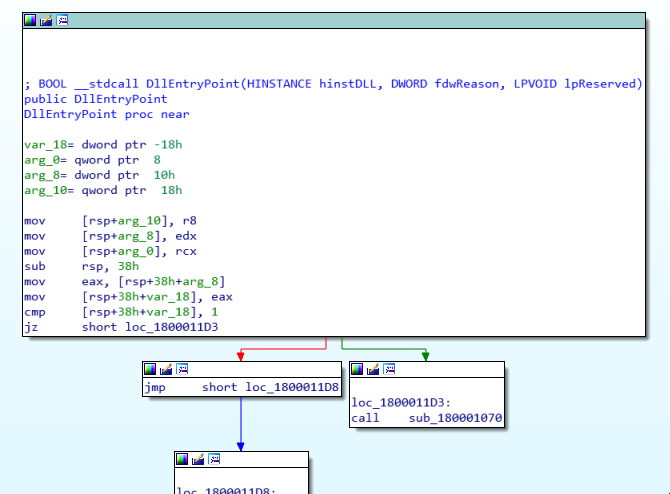
CyberCorp Case 2 part 2 — decoding a base64 gzipped registry payload, tracing PID spoofing in PowerShell, and identifying the reverse shell C2 IP.
Read more →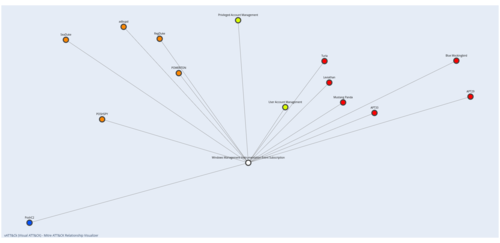
CyberCorp Case 2 threat hunting walkthrough — tracking WMI persistence, a malicious Word document, and a hidden iexproxy.dll download technique in Kibana.
Read more →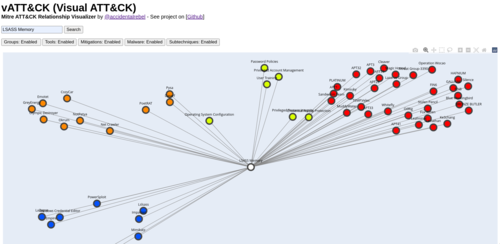
vATT&CK is a visual relationship mapper for MITRE ATT&CK that shows linked malware, threat groups, mitigations, and subtechniques in a single interactive graph.
Read more →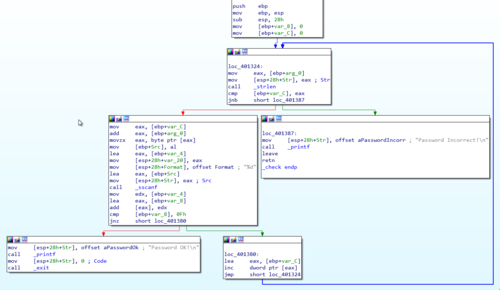
IOLI Crackme 0x04 walkthrough — the password is any digits that sum to 15, revealed by tracing sscanf-based accumulation through static analysis in IDA.
Read more →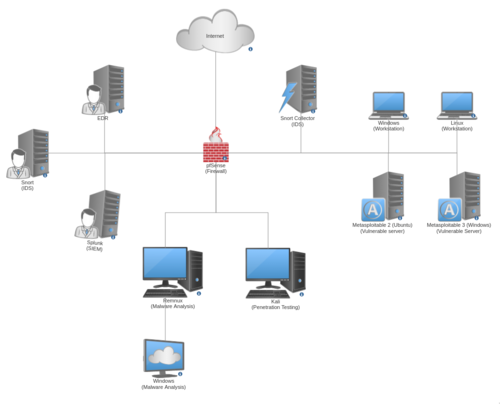
How I built a virtual cybersecurity home lab with pfSense, Metasploitable, Kali, Splunk, Snort, and a dedicated malware analysis network using Remnux.
Read more →