Building RATwurst, a RAT in C and Python, with runtime DLL loading, socket comms, anti-sandbox checks, and basic AV evasion — for educational purposes only.
Read more →Making a RAT


Building RATwurst, a RAT in C and Python, with runtime DLL loading, socket comms, anti-sandbox checks, and basic AV evasion — for educational purposes only.
Read more →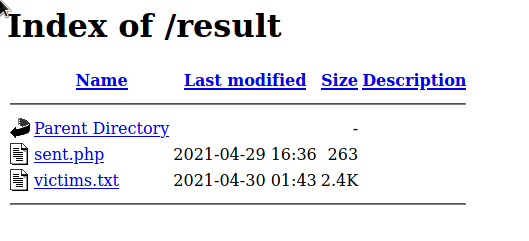
How I found a publicly accessible victims.txt file storing phished Facebook credentials on a 000webhost server and what happened when I reported it.
Read more →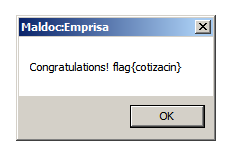
Writeup for the Emprisa Maldoc CTF — analyzing a CVE-2017-18822 exploit using rtfdump, speakeasy shellcode emulation, and EQNEDT32 process debugging.
Read more →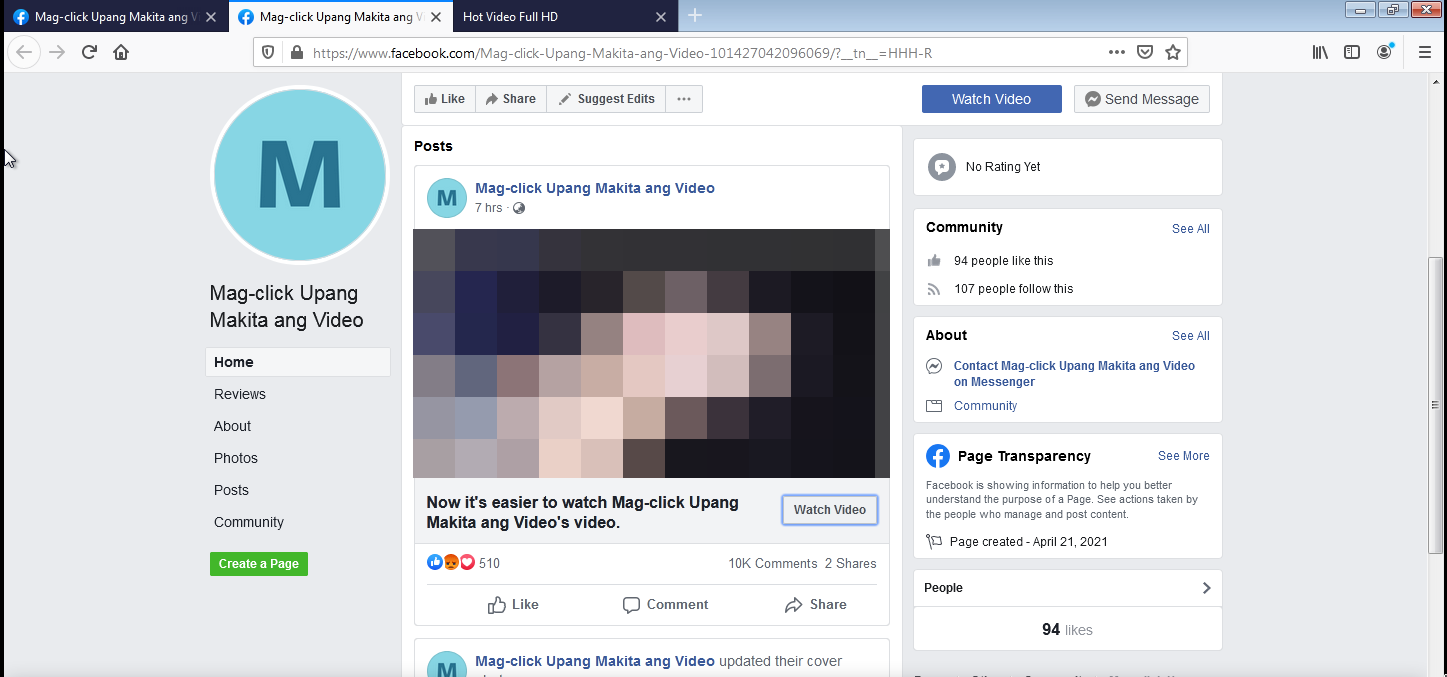
OSINT into a Facebook phishing campaign spreading via friend-tagging — separate hosting domains, Vietnamese code traces, and possible Phishing-as-a-Service.
Read more →
How I turned a real-world malicious document exploit into the Emprisa Maldoc CTF on CyberDefenders — 14 questions targeting intermediate maldoc analysts.
Read more →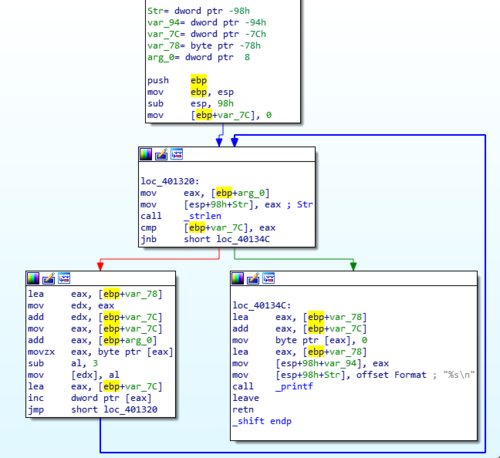
IOLI Crackme 0x03 walkthrough — reverse engineering a Caesar-style cipher that shifts each character by 3 to decode garbled success and failure strings.
Read more →Continuing the Maldoc101 malware analysis — decoding obfuscated VBA string concatenation to reveal WMI class references used for process execution.
Read more →Step-by-step maldoc analysis of the Maldoc101 challenge using oledump and olevba — deobfuscating VBA macros and tracing the WMI process execution chain.
Read more →IOLI Crackme 0x02 walkthrough — computing the password via static analysis of x86 arithmetic, then confirming with dynamic analysis by stepping through IDA.
Read more →shcode2exe converts raw shellcode blobs or strings into debuggable executables targeting 32 or 64-bit Windows, with no Wine dependency when running on Linux.
Read more →