Finding phished passwords on a scam site
Since my last post about my investigations of a Facebook phishing site, I have received several messages from friends asking me to check out other suspected phishing/scam sites. One of the most alarming out of them was this one where I was able to find the file where the scammer stores the phished usernames and passwords.
This particular phishing site conducts its operations like this:
- An ad is shown on Facebook, promising free coupons for famous fast food restaurants
- Clicking on the ad takes the user to a fake Facebook login page hosted on blogger.com
- Login page then sends phished username and passwords to a PHP file hosted on 000webhost
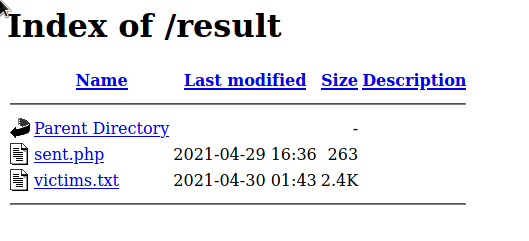
The phished passwords are then stored in a .txt file (blatantly named, victims.txt), which is publicly accessible on an open directory. Getting to this directory involved following the scripts and the URLs used by the scammers. It's …
Investigating an FB phishing site
Last April 21, people were posting warnings about a suspicious Facebook post where your account will supposedly get hacked when you click it. From the discussions, I gathered that it is a classic phishing site scam. A very effective one too, because as soon as an account gets compromised the attacker logs in and tags the friends in the account allowing it to spread further. The news of this got big that even the PH CERT issued a security advisory on it.

I was just curious, I swear!
I wanted to see the phishing site for myself but I was unlucky and did not get tagged by anyone. So I reached out to people who did and I eventually got to this page shown below:
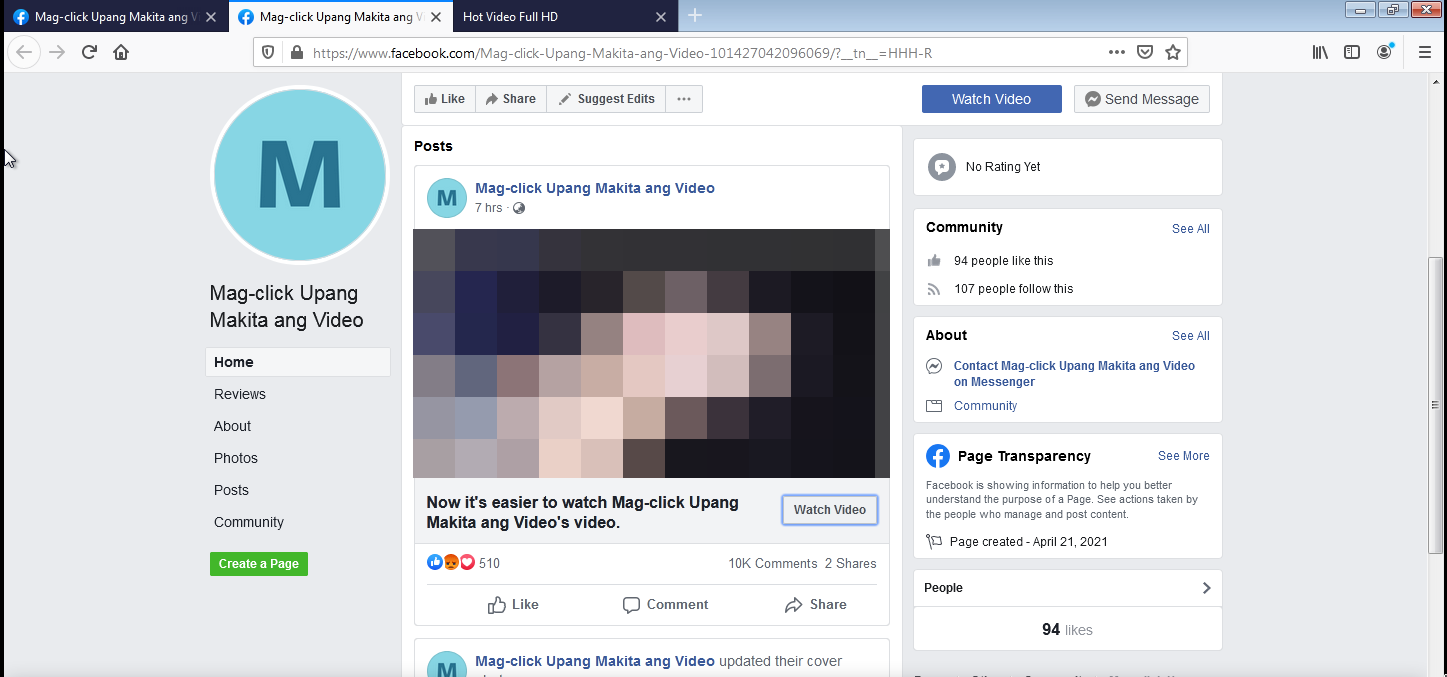
To a trained eye, one could easily see the obvious red flags. But how can one notice them if there is a very attention-catching image …